Dashboard
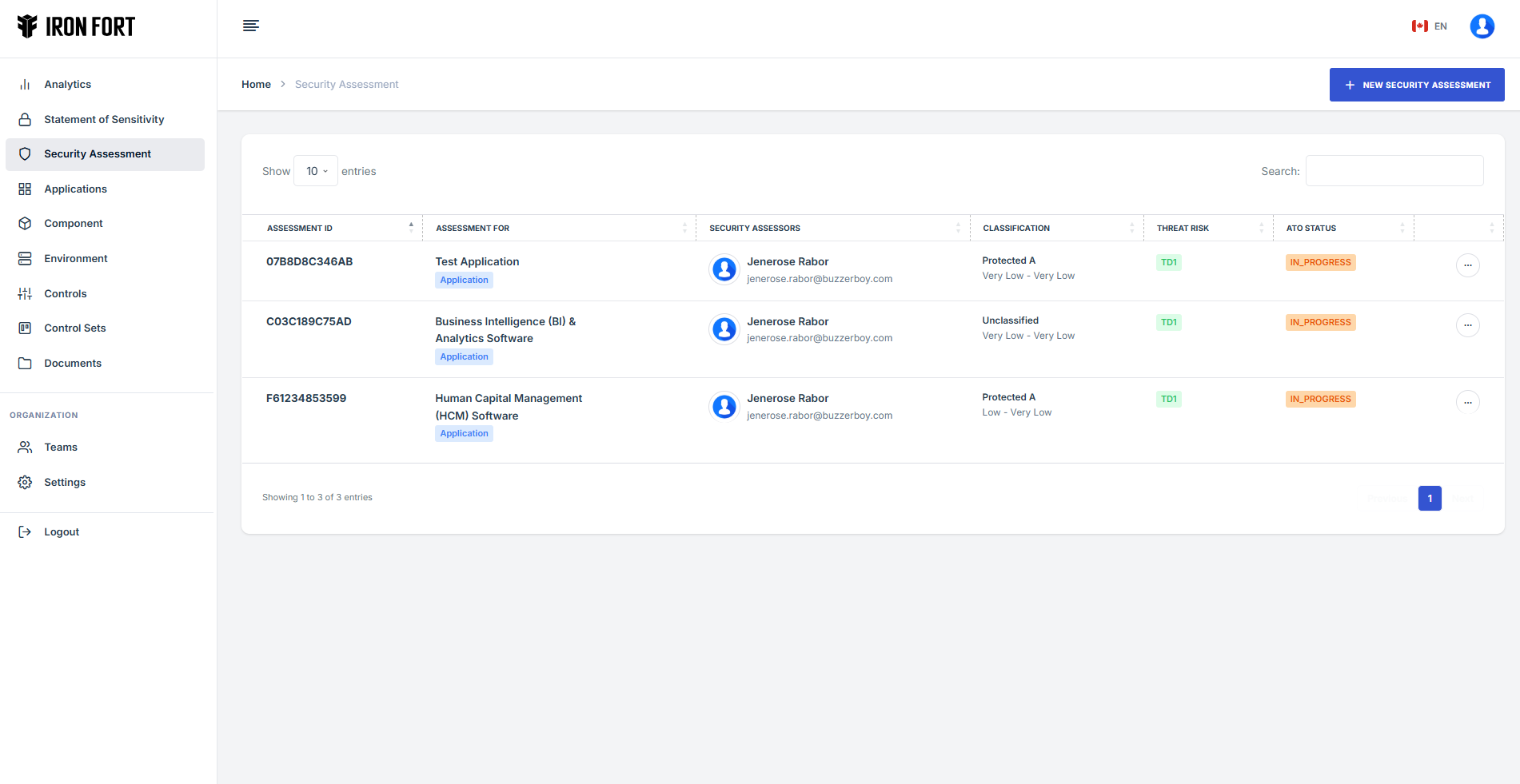
Security Assessment is a structured evaluation of an organization's security controls, policies, and infrastructure to ensure compliance with ITSG-33, ISO standards, PCI-DSS, and other regulatory frameworks. It helps businesses track compliance requirements, manage documentation, and stay audit-ready by organizing essential reports and security policies in one place. The platform also identifies and monitors security vulnerabilities, providing actionable insights to mitigate risks effectively. By streamlining the audit process, Iron Fort ensures that leadership and management have all necessary documentation readily available for third-party auditors. This simplifies compliance tracking, reduces cybersecurity risks, and helps organizations avoid penalties or reputational damage due to non-compliance.



Give it a try
Experience the power of Iron Fort Compliance Security Assessment with a hands-on demo. Discover how our solutions can streamline your compliance processes and improve your organization's security posture.
Security Assessment Topics
Explore various topics related to Iron Fort Compliance Security Assessment, including creation, management, and customization of control sets to meet your compliance needs.
How to plan a new Security Assessment?
Learn the steps to effectively plan a new security assessment to ensure comprehensive coverage and compliance.
What is a security assessment?
Understand the purpose and importance of conducting a security assessment for your organization.
How To: Plan a security assessment?
Step-by-step guide on planning a security assessment to ensure all aspects are covered.
How To: Begin an Assessment?
Instructions on how to initiate a security assessment within the Iron Fort platform.
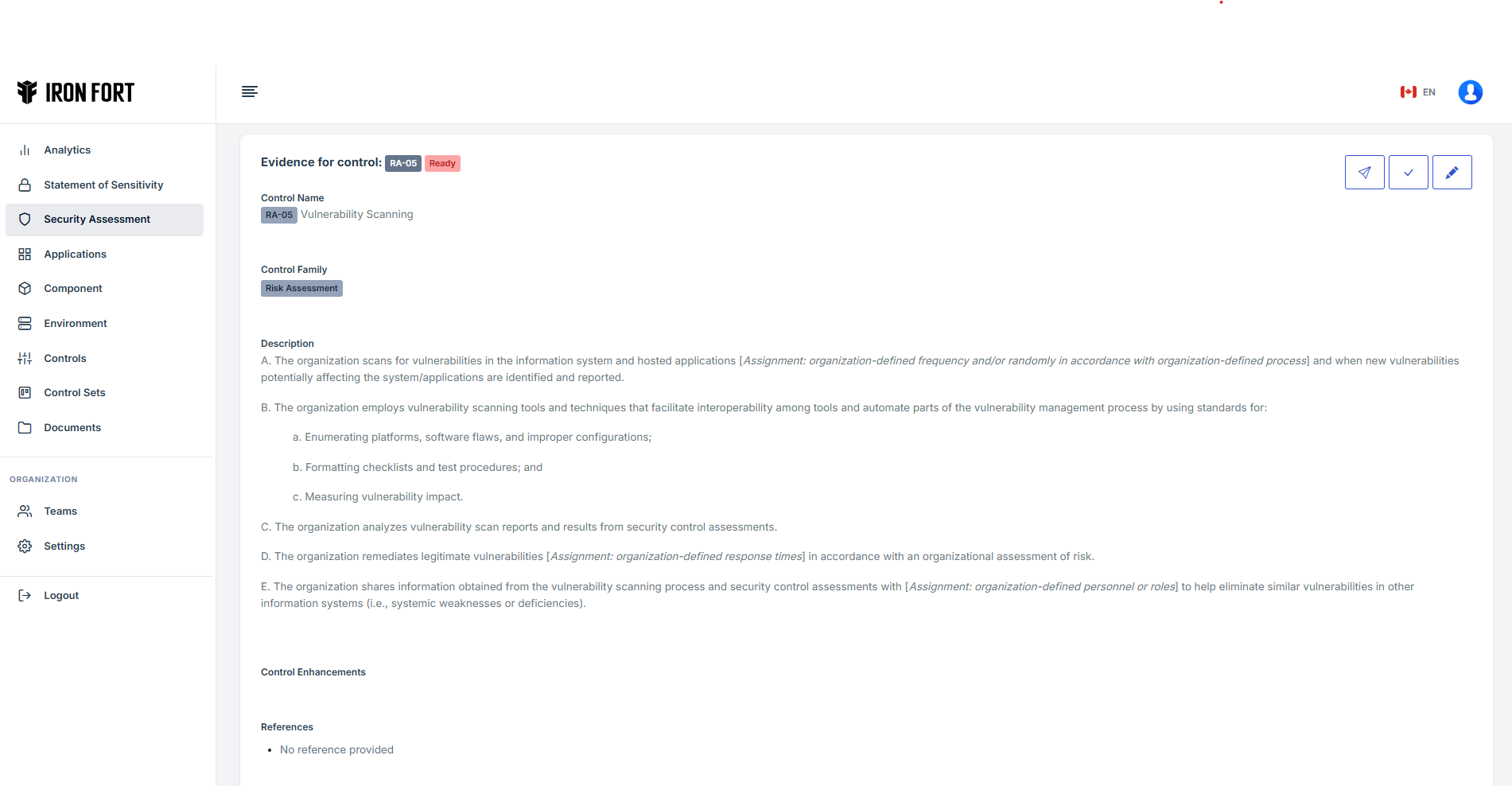
What are evidences?
Learn about the different types of evidence required for a security assessment and their significance.
What is the difference between attached evidence and external evidence?
Understand the distinction between attached evidence and external evidence in the context of a security assessment.
How To: Attach an evidence for a control in a security assessment?
Detailed instructions on how to attach evidence for a specific control during a security assessment.
How To: Attach a link to an internal document to a security assessment for evidence?
Guide on how to link internal documents as evidence in a security assessment.
How To: Submit a control to an assessor?
Steps to submit a control for review by an assessor during a security assessment.
How To: Finalize an assessment and submit it for approval?
Instructions on how to complete and submit a security assessment for final approval.
Ready to Simplify Your Compliance?
Get expert insights on Risk Acceptance in SA&A with our exclusive eBook.
Learn the key factors for managing risk in SA&A. Download our free eBook and simplify your compliance process